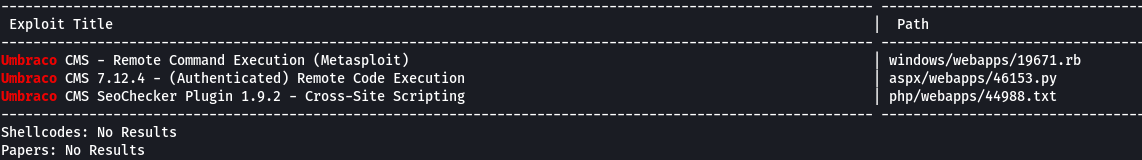
Collection of 2049 port exploit ~ Data will be exchanged over UDP 5004500 protocol IP50 TCP 22 TCP 23 TCP 80 TCP 443 TCP 514 TCP 2049 TCP 2032. A good way to determine this is to issue the command.
as we know it recently is being searched by consumers around us, maybe one of you. People are now accustomed to using the net in gadgets to see image and video data for inspiration, and according to the name of this post I will discuss about 2049 Port Exploit By default the port that the Remote Desktop service runs on is port 3389.
2049 port exploit
Collection of 2049 port exploit ~ NFS Enumeration Port 111 2049 Quick Intro. NFS Enumeration Port 111 2049 Quick Intro. NFS Enumeration Port 111 2049 Quick Intro. NFS Enumeration Port 111 2049 Quick Intro. Network File System NFS - remote filesystem access RFC 1813 RFC5665. Network File System NFS - remote filesystem access RFC 1813 RFC5665. Network File System NFS - remote filesystem access RFC 1813 RFC5665. Network File System NFS - remote filesystem access RFC 1813 RFC5665. TCP guarantees delivery of data packets on port 2049 in the same order in. TCP guarantees delivery of data packets on port 2049 in the same order in. TCP guarantees delivery of data packets on port 2049 in the same order in. TCP guarantees delivery of data packets on port 2049 in the same order in.
To allow remote access from any host a standard rhosts situation. To allow remote access from any host a standard rhosts situation. To allow remote access from any host a standard rhosts situation. To allow remote access from any host a standard rhosts situation. Showmount -e IP_Address. Showmount -e IP_Address. Showmount -e IP_Address. Showmount -e IP_Address. On Unix-like operating systems a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. On Unix-like operating systems a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. On Unix-like operating systems a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. On Unix-like operating systems a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports.
Here is the tutorial for the exploit. Here is the tutorial for the exploit. Here is the tutorial for the exploit. Here is the tutorial for the exploit. There are many steps you can take to harden the NFS service however for this particular machine I just added iptables commands to block the Kali machines IP from attempting to mount the Metasploitable machine. There are many steps you can take to harden the NFS service however for this particular machine I just added iptables commands to block the Kali machines IP from attempting to mount the Metasploitable machine. There are many steps you can take to harden the NFS service however for this particular machine I just added iptables commands to block the Kali machines IP from attempting to mount the Metasploitable machine. There are many steps you can take to harden the NFS service however for this particular machine I just added iptables commands to block the Kali machines IP from attempting to mount the Metasploitable machine. A commonly scanned and exploited attack vector. A commonly scanned and exploited attack vector. A commonly scanned and exploited attack vector. A commonly scanned and exploited attack vector.
UDP port 2049 would not have guaranteed communication in the same way as TCP. UDP port 2049 would not have guaranteed communication in the same way as TCP. UDP port 2049 would not have guaranteed communication in the same way as TCP. UDP port 2049 would not have guaranteed communication in the same way as TCP. Rpcinfo -p 1921681112 grep nfs. Rpcinfo -p 1921681112 grep nfs. Rpcinfo -p 1921681112 grep nfs. Rpcinfo -p 1921681112 grep nfs. Mountd is forced to bind to port 32767. Mountd is forced to bind to port 32767. Mountd is forced to bind to port 32767. Mountd is forced to bind to port 32767.
Note that for this exploit you need to first install nfs-common with apt-get-install nfs-common on your Kali Linux machine. Note that for this exploit you need to first install nfs-common with apt-get-install nfs-common on your Kali Linux machine. Note that for this exploit you need to first install nfs-common with apt-get-install nfs-common on your Kali Linux machine. Note that for this exploit you need to first install nfs-common with apt-get-install nfs-common on your Kali Linux machine. We are not using quotas. We are not using quotas. We are not using quotas. We are not using quotas. Exploit and connect to port 512 513 and 514 October 27 2019 Exploit and connect to port 512 513 and 514 Unix Basics. Exploit and connect to port 512 513 and 514 October 27 2019 Exploit and connect to port 512 513 and 514 Unix Basics. Exploit and connect to port 512 513 and 514 October 27 2019 Exploit and connect to port 512 513 and 514 Unix Basics. Exploit and connect to port 512 513 and 514 October 27 2019 Exploit and connect to port 512 513 and 514 Unix Basics.
It can be observed that the Windows machine with IP Address 192168141 has Remote Desktop Service successfully. It can be observed that the Windows machine with IP Address 192168141 has Remote Desktop Service successfully. It can be observed that the Windows machine with IP Address 192168141 has Remote Desktop Service successfully. It can be observed that the Windows machine with IP Address 192168141 has Remote Desktop Service successfully. Because protocol TCP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol TCP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol TCP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol TCP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. 8 rows The Exploit Database is a CVE compliant archive of public exploits and corresponding. 8 rows The Exploit Database is a CVE compliant archive of public exploits and corresponding. 8 rows The Exploit Database is a CVE compliant archive of public exploits and corresponding. 8 rows The Exploit Database is a CVE compliant archive of public exploits and corresponding.
Ssh runs on port 22. Ssh runs on port 22. Ssh runs on port 22. Ssh runs on port 22. You could try ms08-067-netapi for XP or EternalBlue for most x64 windows targets Unless you have some better code like I just finished or for linux targets you could try some Samba exploits though. You could try ms08-067-netapi for XP or EternalBlue for most x64 windows targets Unless you have some better code like I just finished or for linux targets you could try some Samba exploits though. You could try ms08-067-netapi for XP or EternalBlue for most x64 windows targets Unless you have some better code like I just finished or for linux targets you could try some Samba exploits though. You could try ms08-067-netapi for XP or EternalBlue for most x64 windows targets Unless you have some better code like I just finished or for linux targets you could try some Samba exploits though. In Redhat ports will change when each time NFS is restarted. In Redhat ports will change when each time NFS is restarted. In Redhat ports will change when each time NFS is restarted. In Redhat ports will change when each time NFS is restarted.
Port 2049 - NFS. Port 2049 - NFS. Port 2049 - NFS. Port 2049 - NFS. Developed in 1984 by Sun Microsystem and similar to SMB because it allows access to files over a network. Developed in 1984 by Sun Microsystem and similar to SMB because it allows access to files over a network. Developed in 1984 by Sun Microsystem and similar to SMB because it allows access to files over a network. Developed in 1984 by Sun Microsystem and similar to SMB because it allows access to files over a network. Badges Porting BlueKeep PoC from Ekultek umarfarook882 to actual exploits. Badges Porting BlueKeep PoC from Ekultek umarfarook882 to actual exploits. Badges Porting BlueKeep PoC from Ekultek umarfarook882 to actual exploits. Badges Porting BlueKeep PoC from Ekultek umarfarook882 to actual exploits.
Script kiddies are not welcomed here as at anywhere else. Script kiddies are not welcomed here as at anywhere else. Script kiddies are not welcomed here as at anywhere else. Script kiddies are not welcomed here as at anywhere else. It is also able to extract the System Name of the Machine it is MSEDGEWIN10. It is also able to extract the System Name of the Machine it is MSEDGEWIN10. It is also able to extract the System Name of the Machine it is MSEDGEWIN10. It is also able to extract the System Name of the Machine it is MSEDGEWIN10. Lockds module parameters have been set to bind to 32768. Lockds module parameters have been set to bind to 32768. Lockds module parameters have been set to bind to 32768. Lockds module parameters have been set to bind to 32768.
TCP is one of the main protocols in TCPIP networks. TCP is one of the main protocols in TCPIP networks. TCP is one of the main protocols in TCPIP networks. TCP is one of the main protocols in TCPIP networks. Rerun the scan with. Rerun the scan with. Rerun the scan with. Rerun the scan with. AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database.
Splunk - Remote Command Execution. Splunk - Remote Command Execution. Splunk - Remote Command Execution. Splunk - Remote Command Execution. To take advantage of this make sure the rsh-client client is installed on Ubuntu and. To take advantage of this make sure the rsh-client client is installed on Ubuntu and. To take advantage of this make sure the rsh-client client is installed on Ubuntu and. To take advantage of this make sure the rsh-client client is installed on Ubuntu and. When the client is done it updates its own mount tables but doesnt inform the server. When the client is done it updates its own mount tables but doesnt inform the server. When the client is done it updates its own mount tables but doesnt inform the server. When the client is done it updates its own mount tables but doesnt inform the server.
TCP ports 512 513 and 514 are known as r services and have been misconfigured. TCP ports 512 513 and 514 are known as r services and have been misconfigured. TCP ports 512 513 and 514 are known as r services and have been misconfigured. TCP ports 512 513 and 514 are known as r services and have been misconfigured. Remote exploit for Multiple platform. Remote exploit for Multiple platform. Remote exploit for Multiple platform. Remote exploit for Multiple platform. Typically this is port 2049 Whenever the client wants to make a request to the NFS server for example to read a directory an RPC is sent to the NFS server. Typically this is port 2049 Whenever the client wants to make a request to the NFS server for example to read a directory an RPC is sent to the NFS server. Typically this is port 2049 Whenever the client wants to make a request to the NFS server for example to read a directory an RPC is sent to the NFS server. Typically this is port 2049 Whenever the client wants to make a request to the NFS server for example to read a directory an RPC is sent to the NFS server.
Welcome to Join our Discord ServerPlease note that this is not yet an exploit but rather an attempt to port existing PoCs to actual exploits. Welcome to Join our Discord ServerPlease note that this is not yet an exploit but rather an attempt to port existing PoCs to actual exploits. Welcome to Join our Discord ServerPlease note that this is not yet an exploit but rather an attempt to port existing PoCs to actual exploits. Welcome to Join our Discord ServerPlease note that this is not yet an exploit but rather an attempt to port existing PoCs to actual exploits. Nfs daemon doesnt listen 2049 portHelpful. Nfs daemon doesnt listen 2049 portHelpful. Nfs daemon doesnt listen 2049 portHelpful. Nfs daemon doesnt listen 2049 portHelpful. Because protocol UDP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol UDP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol UDP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol UDP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate.
The rpcinfo command makes an RPC call to an RPC. The rpcinfo command makes an RPC call to an RPC. The rpcinfo command makes an RPC call to an RPC. The rpcinfo command makes an RPC call to an RPC. 2049 Oak Ave Port Arthur TX 77642. 2049 Oak Ave Port Arthur TX 77642. 2049 Oak Ave Port Arthur TX 77642. 2049 Oak Ave Port Arthur TX 77642. As in the example above statd has been started so that it only binds to port 32765 for incoming requests and it must answer on port 32766. As in the example above statd has been started so that it only binds to port 32765 for incoming requests and it must answer on port 32766. As in the example above statd has been started so that it only binds to port 32765 for incoming requests and it must answer on port 32766. As in the example above statd has been started so that it only binds to port 32765 for incoming requests and it must answer on port 32766.
They are used by system processes that provide widely used types of network services. They are used by system processes that provide widely used types of network services. They are used by system processes that provide widely used types of network services. They are used by system processes that provide widely used types of network services. Use of NFS on a system can be determined if port 2049 is open this is a good indication but it doesnt actually prove any folders are being offered. Use of NFS on a system can be determined if port 2049 is open this is a good indication but it doesnt actually prove any folders are being offered. Use of NFS on a system can be determined if port 2049 is open this is a good indication but it doesnt actually prove any folders are being offered. Use of NFS on a system can be determined if port 2049 is open this is a good indication but it doesnt actually prove any folders are being offered. Why does some exploits have keysystems. Why does some exploits have keysystems. Why does some exploits have keysystems. Why does some exploits have keysystems.
Nmap -sV -O and report what it returns. Nmap -sV -O and report what it returns. Nmap -sV -O and report what it returns. Nmap -sV -O and report what it returns. Only when a connection is set up users data can be sent bi-directionally over the connection. Only when a connection is set up users data can be sent bi-directionally over the connection. Only when a connection is set up users data can be sent bi-directionally over the connection. Only when a connection is set up users data can be sent bi-directionally over the connection. We do our best to provide you with accurate information on PORT 2049 and work hard to keep our database up to date. We do our best to provide you with accurate information on PORT 2049 and work hard to keep our database up to date. We do our best to provide you with accurate information on PORT 2049 and work hard to keep our database up to date. We do our best to provide you with accurate information on PORT 2049 and work hard to keep our database up to date.
Please support me on Patreon. Please support me on Patreon. Please support me on Patreon. Please support me on Patreon. The Project 2049 Institute is a nonprofit research organization focused on promoting American values and security interests in the Indo-Pacific region. The Project 2049 Institute is a nonprofit research organization focused on promoting American values and security interests in the Indo-Pacific region. The Project 2049 Institute is a nonprofit research organization focused on promoting American values and security interests in the Indo-Pacific region. The Project 2049 Institute is a nonprofit research organization focused on promoting American values and security interests in the Indo-Pacific region. Rpcbind runs on port 111 for both TCP and UDP. Rpcbind runs on port 111 for both TCP and UDP. Rpcbind runs on port 111 for both TCP and UDP. Rpcbind runs on port 111 for both TCP and UDP.
About Port Exploit 8080. About Port Exploit 8080. About Port Exploit 8080. About Port Exploit 8080. According to the Port Arthur. According to the Port Arthur. According to the Port Arthur. According to the Port Arthur. Nmap -A -p3389 192168141. Nmap -A -p3389 192168141. Nmap -A -p3389 192168141. Nmap -A -p3389 192168141.
Nfs runs on port 2049 for both TCP and UDP. Nfs runs on port 2049 for both TCP and UDP. Nfs runs on port 2049 for both TCP and UDP. Nfs runs on port 2049 for both TCP and UDP. We can assign a permanent port number to each. We can assign a permanent port number to each. We can assign a permanent port number to each. We can assign a permanent port number to each. Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly. Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly. Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly. Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly.
Syslog will be sent into an IPSec tunnel. Syslog will be sent into an IPSec tunnel. Syslog will be sent into an IPSec tunnel. Syslog will be sent into an IPSec tunnel. Guaranteed communication over port 2049 is the key difference between TCP and UDP. Guaranteed communication over port 2049 is the key difference between TCP and UDP. Guaranteed communication over port 2049 is the key difference between TCP and UDP. Guaranteed communication over port 2049 is the key difference between TCP and UDP. Conduct a NFS Assessment. Conduct a NFS Assessment. Conduct a NFS Assessment. Conduct a NFS Assessment.
D0wnp0ur 3 years ago Well it all depends. D0wnp0ur 3 years ago Well it all depends. D0wnp0ur 3 years ago Well it all depends. D0wnp0ur 3 years ago Well it all depends. Common ports used by NFS are port 111 and 2049. Common ports used by NFS are port 111 and 2049. Common ports used by NFS are port 111 and 2049. Common ports used by NFS are port 111 and 2049. TCP 3000 TCP 514 UDP137-139 and TCP 445 UDP 514 NoteIf a secure connection has been configured between a FortiGate and FortiAnalyzer. TCP 3000 TCP 514 UDP137-139 and TCP 445 UDP 514 NoteIf a secure connection has been configured between a FortiGate and FortiAnalyzer. TCP 3000 TCP 514 UDP137-139 and TCP 445 UDP 514 NoteIf a secure connection has been configured between a FortiGate and FortiAnalyzer. TCP 3000 TCP 514 UDP137-139 and TCP 445 UDP 514 NoteIf a secure connection has been configured between a FortiGate and FortiAnalyzer.
If you are search for Port 8080 Exploit simply cheking out our text below. If you are search for Port 8080 Exploit simply cheking out our text below. If you are search for Port 8080 Exploit simply cheking out our text below. If you are search for Port 8080 Exploit simply cheking out our text below. FortiAnalyzer FDN ports Vulnerability Management updates. FortiAnalyzer FDN ports Vulnerability Management updates. FortiAnalyzer FDN ports Vulnerability Management updates. FortiAnalyzer FDN ports Vulnerability Management updates. If you are like me i search the ports and its exploits on google. If you are like me i search the ports and its exploits on google. If you are like me i search the ports and its exploits on google. If you are like me i search the ports and its exploits on google.
Hopefully the expectant results will look something like this. Hopefully the expectant results will look something like this. Hopefully the expectant results will look something like this. Hopefully the expectant results will look something like this. Replace 1921681112 with metasploitables IP address obtained from Section 2 Step 2. Replace 1921681112 with metasploitables IP address obtained from Section 2 Step 2. Replace 1921681112 with metasploitables IP address obtained from Section 2 Step 2. Replace 1921681112 with metasploitables IP address obtained from Section 2 Step 2. The port numbers in the range from 0 to 1023 0 to 2 10 1 are the well-known ports or system ports. The port numbers in the range from 0 to 1023 0 to 2 10 1 are the well-known ports or system ports. The port numbers in the range from 0 to 1023 0 to 2 10 1 are the well-known ports or system ports. The port numbers in the range from 0 to 1023 0 to 2 10 1 are the well-known ports or system ports.
Port Exploit 8080. Port Exploit 8080. Port Exploit 8080. Port Exploit 8080. We specialize in open-source research using Chinese language sources to inform policy debate and advance public education. We specialize in open-source research using Chinese language sources to inform policy debate and advance public education. We specialize in open-source research using Chinese language sources to inform policy debate and advance public education. We specialize in open-source research using Chinese language sources to inform policy debate and advance public education. Configure NFSv3 Ports in RedHat. Configure NFSv3 Ports in RedHat. Configure NFSv3 Ports in RedHat. Configure NFSv3 Ports in RedHat.
The main reason is to support the developer for there hard work also for new stuff. The main reason is to support the developer for there hard work also for new stuff. The main reason is to support the developer for there hard work also for new stuff. The main reason is to support the developer for there hard work also for new stuff. If available please supply below. If available please supply below. If available please supply below. If available please supply below. Nfsd is of course on port 2049 and the portmapper is on port 111. Nfsd is of course on port 2049 and the portmapper is on port 111. Nfsd is of course on port 2049 and the portmapper is on port 111. Nfsd is of course on port 2049 and the portmapper is on port 111.
Our core mission is to create and disseminate knowledge that makes the region more peaceful and prosperous. Our core mission is to create and disseminate knowledge that makes the region more peaceful and prosperous. Our core mission is to create and disseminate knowledge that makes the region more peaceful and prosperous. Our core mission is to create and disseminate knowledge that makes the region more peaceful and prosperous. TCP is a connection-oriented protocol it requires handshaking to set up end-to-end communications. TCP is a connection-oriented protocol it requires handshaking to set up end-to-end communications. TCP is a connection-oriented protocol it requires handshaking to set up end-to-end communications. TCP is a connection-oriented protocol it requires handshaking to set up end-to-end communications. This is becus roblox updated every week and all the codes in the exploit are getting patched thats why the injection is broke at that moment thats why you need to check the website again to see if the exploit is updated this will also be told in the card of the exploit. This is becus roblox updated every week and all the codes in the exploit are getting patched thats why the injection is broke at that moment thats why you need to check the website again to see if the exploit is updated this will also be told in the card of the exploit. This is becus roblox updated every week and all the codes in the exploit are getting patched thats why the injection is broke at that moment thats why you need to check the website again to see if the exploit is updated this will also be told in the card of the exploit. This is becus roblox updated every week and all the codes in the exploit are getting patched thats why the injection is broke at that moment thats why you need to check the website again to see if the exploit is updated this will also be told in the card of the exploit.
TCP port 2049 uses the Transmission Control Protocol. TCP port 2049 uses the Transmission Control Protocol. TCP port 2049 uses the Transmission Control Protocol. TCP port 2049 uses the Transmission Control Protocol. Property Overview - The 144700 estimated value is 014 less than the median listing price of 144900 for the Rose Farm area. Property Overview - The 144700 estimated value is 014 less than the median listing price of 144900 for the Rose Farm area. Property Overview - The 144700 estimated value is 014 less than the median listing price of 144900 for the Rose Farm area. Property Overview - The 144700 estimated value is 014 less than the median listing price of 144900 for the Rose Farm area. This is a free service and accuracy is. This is a free service and accuracy is. This is a free service and accuracy is. This is a free service and accuracy is.
2
Source Image @

2049 port exploit | 2
Collection of 2049 port exploit ~ NFS Enumeration Port 111 2049 Quick Intro. NFS Enumeration Port 111 2049 Quick Intro. NFS Enumeration Port 111 2049 Quick Intro. Network File System NFS - remote filesystem access RFC 1813 RFC5665. Network File System NFS - remote filesystem access RFC 1813 RFC5665. Network File System NFS - remote filesystem access RFC 1813 RFC5665. TCP guarantees delivery of data packets on port 2049 in the same order in. TCP guarantees delivery of data packets on port 2049 in the same order in. TCP guarantees delivery of data packets on port 2049 in the same order in.
To allow remote access from any host a standard rhosts situation. To allow remote access from any host a standard rhosts situation. To allow remote access from any host a standard rhosts situation. Showmount -e IP_Address. Showmount -e IP_Address. Showmount -e IP_Address. On Unix-like operating systems a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. On Unix-like operating systems a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. On Unix-like operating systems a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports.
Here is the tutorial for the exploit. Here is the tutorial for the exploit. Here is the tutorial for the exploit. There are many steps you can take to harden the NFS service however for this particular machine I just added iptables commands to block the Kali machines IP from attempting to mount the Metasploitable machine. There are many steps you can take to harden the NFS service however for this particular machine I just added iptables commands to block the Kali machines IP from attempting to mount the Metasploitable machine. There are many steps you can take to harden the NFS service however for this particular machine I just added iptables commands to block the Kali machines IP from attempting to mount the Metasploitable machine. A commonly scanned and exploited attack vector. A commonly scanned and exploited attack vector. A commonly scanned and exploited attack vector.
UDP port 2049 would not have guaranteed communication in the same way as TCP. UDP port 2049 would not have guaranteed communication in the same way as TCP. UDP port 2049 would not have guaranteed communication in the same way as TCP. Rpcinfo -p 1921681112 grep nfs. Rpcinfo -p 1921681112 grep nfs. Rpcinfo -p 1921681112 grep nfs. Mountd is forced to bind to port 32767. Mountd is forced to bind to port 32767. Mountd is forced to bind to port 32767.
Note that for this exploit you need to first install nfs-common with apt-get-install nfs-common on your Kali Linux machine. Note that for this exploit you need to first install nfs-common with apt-get-install nfs-common on your Kali Linux machine. Note that for this exploit you need to first install nfs-common with apt-get-install nfs-common on your Kali Linux machine. We are not using quotas. We are not using quotas. We are not using quotas. Exploit and connect to port 512 513 and 514 October 27 2019 Exploit and connect to port 512 513 and 514 Unix Basics. Exploit and connect to port 512 513 and 514 October 27 2019 Exploit and connect to port 512 513 and 514 Unix Basics. Exploit and connect to port 512 513 and 514 October 27 2019 Exploit and connect to port 512 513 and 514 Unix Basics.
It can be observed that the Windows machine with IP Address 192168141 has Remote Desktop Service successfully. It can be observed that the Windows machine with IP Address 192168141 has Remote Desktop Service successfully. It can be observed that the Windows machine with IP Address 192168141 has Remote Desktop Service successfully. Because protocol TCP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol TCP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol TCP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. 8 rows The Exploit Database is a CVE compliant archive of public exploits and corresponding. 8 rows The Exploit Database is a CVE compliant archive of public exploits and corresponding. 8 rows The Exploit Database is a CVE compliant archive of public exploits and corresponding.
Ssh runs on port 22. Ssh runs on port 22. Ssh runs on port 22. You could try ms08-067-netapi for XP or EternalBlue for most x64 windows targets Unless you have some better code like I just finished or for linux targets you could try some Samba exploits though. You could try ms08-067-netapi for XP or EternalBlue for most x64 windows targets Unless you have some better code like I just finished or for linux targets you could try some Samba exploits though. You could try ms08-067-netapi for XP or EternalBlue for most x64 windows targets Unless you have some better code like I just finished or for linux targets you could try some Samba exploits though. In Redhat ports will change when each time NFS is restarted. In Redhat ports will change when each time NFS is restarted. In Redhat ports will change when each time NFS is restarted.
Port 2049 - NFS. Port 2049 - NFS. Port 2049 - NFS. Developed in 1984 by Sun Microsystem and similar to SMB because it allows access to files over a network. Developed in 1984 by Sun Microsystem and similar to SMB because it allows access to files over a network. Developed in 1984 by Sun Microsystem and similar to SMB because it allows access to files over a network. Badges Porting BlueKeep PoC from Ekultek umarfarook882 to actual exploits. Badges Porting BlueKeep PoC from Ekultek umarfarook882 to actual exploits. Badges Porting BlueKeep PoC from Ekultek umarfarook882 to actual exploits.
Script kiddies are not welcomed here as at anywhere else. Script kiddies are not welcomed here as at anywhere else. Script kiddies are not welcomed here as at anywhere else. It is also able to extract the System Name of the Machine it is MSEDGEWIN10. It is also able to extract the System Name of the Machine it is MSEDGEWIN10. It is also able to extract the System Name of the Machine it is MSEDGEWIN10. Lockds module parameters have been set to bind to 32768. Lockds module parameters have been set to bind to 32768. Lockds module parameters have been set to bind to 32768.
TCP is one of the main protocols in TCPIP networks. TCP is one of the main protocols in TCPIP networks. TCP is one of the main protocols in TCPIP networks. Rerun the scan with. Rerun the scan with. Rerun the scan with. AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database. AttackerKB requires a CVE ID in order to pull vulnerability data and references from the CVE list and the National Vulnerability Database.
Splunk - Remote Command Execution. Splunk - Remote Command Execution. Splunk - Remote Command Execution. To take advantage of this make sure the rsh-client client is installed on Ubuntu and. To take advantage of this make sure the rsh-client client is installed on Ubuntu and. To take advantage of this make sure the rsh-client client is installed on Ubuntu and. When the client is done it updates its own mount tables but doesnt inform the server. When the client is done it updates its own mount tables but doesnt inform the server. When the client is done it updates its own mount tables but doesnt inform the server.
TCP ports 512 513 and 514 are known as r services and have been misconfigured. TCP ports 512 513 and 514 are known as r services and have been misconfigured. TCP ports 512 513 and 514 are known as r services and have been misconfigured. Remote exploit for Multiple platform. Remote exploit for Multiple platform. Remote exploit for Multiple platform. Typically this is port 2049 Whenever the client wants to make a request to the NFS server for example to read a directory an RPC is sent to the NFS server. Typically this is port 2049 Whenever the client wants to make a request to the NFS server for example to read a directory an RPC is sent to the NFS server. Typically this is port 2049 Whenever the client wants to make a request to the NFS server for example to read a directory an RPC is sent to the NFS server.
Welcome to Join our Discord ServerPlease note that this is not yet an exploit but rather an attempt to port existing PoCs to actual exploits. Welcome to Join our Discord ServerPlease note that this is not yet an exploit but rather an attempt to port existing PoCs to actual exploits. Welcome to Join our Discord ServerPlease note that this is not yet an exploit but rather an attempt to port existing PoCs to actual exploits. Nfs daemon doesnt listen 2049 portHelpful. Nfs daemon doesnt listen 2049 portHelpful. Nfs daemon doesnt listen 2049 portHelpful. Because protocol UDP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol UDP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate. Because protocol UDP port 2049 was flagged as a virus colored red does not mean that a virus is using port 2049 but that a Trojan or Virus has used this port in the past to communicate.
The rpcinfo command makes an RPC call to an RPC. The rpcinfo command makes an RPC call to an RPC. The rpcinfo command makes an RPC call to an RPC. 2049 Oak Ave Port Arthur TX 77642. 2049 Oak Ave Port Arthur TX 77642. 2049 Oak Ave Port Arthur TX 77642. As in the example above statd has been started so that it only binds to port 32765 for incoming requests and it must answer on port 32766. As in the example above statd has been started so that it only binds to port 32765 for incoming requests and it must answer on port 32766. As in the example above statd has been started so that it only binds to port 32765 for incoming requests and it must answer on port 32766.
They are used by system processes that provide widely used types of network services. They are used by system processes that provide widely used types of network services. They are used by system processes that provide widely used types of network services. Use of NFS on a system can be determined if port 2049 is open this is a good indication but it doesnt actually prove any folders are being offered. Use of NFS on a system can be determined if port 2049 is open this is a good indication but it doesnt actually prove any folders are being offered. Use of NFS on a system can be determined if port 2049 is open this is a good indication but it doesnt actually prove any folders are being offered. Why does some exploits have keysystems. Why does some exploits have keysystems. Why does some exploits have keysystems.
Nmap -sV -O and report what it returns. Nmap -sV -O and report what it returns. Nmap -sV -O and report what it returns. Only when a connection is set up users data can be sent bi-directionally over the connection. Only when a connection is set up users data can be sent bi-directionally over the connection. Only when a connection is set up users data can be sent bi-directionally over the connection. We do our best to provide you with accurate information on PORT 2049 and work hard to keep our database up to date. We do our best to provide you with accurate information on PORT 2049 and work hard to keep our database up to date. We do our best to provide you with accurate information on PORT 2049 and work hard to keep our database up to date.
Please support me on Patreon. Please support me on Patreon. Please support me on Patreon. The Project 2049 Institute is a nonprofit research organization focused on promoting American values and security interests in the Indo-Pacific region. The Project 2049 Institute is a nonprofit research organization focused on promoting American values and security interests in the Indo-Pacific region. The Project 2049 Institute is a nonprofit research organization focused on promoting American values and security interests in the Indo-Pacific region. Rpcbind runs on port 111 for both TCP and UDP. Rpcbind runs on port 111 for both TCP and UDP. Rpcbind runs on port 111 for both TCP and UDP.
About Port Exploit 8080. About Port Exploit 8080. About Port Exploit 8080. According to the Port Arthur. According to the Port Arthur. According to the Port Arthur. Nmap -A -p3389 192168141. Nmap -A -p3389 192168141. Nmap -A -p3389 192168141.
Nfs runs on port 2049 for both TCP and UDP. Nfs runs on port 2049 for both TCP and UDP. Nfs runs on port 2049 for both TCP and UDP. We can assign a permanent port number to each. We can assign a permanent port number to each. We can assign a permanent port number to each. Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly. Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly. Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly.
Syslog will be sent into an IPSec tunnel. Syslog will be sent into an IPSec tunnel. Syslog will be sent into an IPSec tunnel. Guaranteed communication over port 2049 is the key difference between TCP and UDP. Guaranteed communication over port 2049 is the key difference between TCP and UDP. Guaranteed communication over port 2049 is the key difference between TCP and UDP. Conduct a NFS Assessment. Conduct a NFS Assessment. Conduct a NFS Assessment.
D0wnp0ur 3 years ago Well it all depends. D0wnp0ur 3 years ago Well it all depends. D0wnp0ur 3 years ago Well it all depends. Common ports used by NFS are port 111 and 2049. Common ports used by NFS are port 111 and 2049. Common ports used by NFS are port 111 and 2049. TCP 3000 TCP 514 UDP137-139 and TCP 445 UDP 514 NoteIf a secure connection has been configured between a FortiGate and FortiAnalyzer. TCP 3000 TCP 514 UDP137-139 and TCP 445 UDP 514 NoteIf a secure connection has been configured between a FortiGate and FortiAnalyzer. TCP 3000 TCP 514 UDP137-139 and TCP 445 UDP 514 NoteIf a secure connection has been configured between a FortiGate and FortiAnalyzer.
If you are search for Port 8080 Exploit simply cheking out our text below. If you are search for Port 8080 Exploit simply cheking out our text below. If you are search for Port 8080 Exploit simply cheking out our text below. FortiAnalyzer FDN ports Vulnerability Management updates. FortiAnalyzer FDN ports Vulnerability Management updates. FortiAnalyzer FDN ports Vulnerability Management updates. If you are like me i search the ports and its exploits on google. If you are like me i search the ports and its exploits on google. If you are like me i search the ports and its exploits on google.
Hopefully the expectant results will look something like this. Hopefully the expectant results will look something like this. Hopefully the expectant results will look something like this. Replace 1921681112 with metasploitables IP address obtained from Section 2 Step 2. Replace 1921681112 with metasploitables IP address obtained from Section 2 Step 2. Replace 1921681112 with metasploitables IP address obtained from Section 2 Step 2. The port numbers in the range from 0 to 1023 0 to 2 10 1 are the well-known ports or system ports. The port numbers in the range from 0 to 1023 0 to 2 10 1 are the well-known ports or system ports. The port numbers in the range from 0 to 1023 0 to 2 10 1 are the well-known ports or system ports.
Port Exploit 8080. Port Exploit 8080. Port Exploit 8080. We specialize in open-source research using Chinese language sources to inform policy debate and advance public education. We specialize in open-source research using Chinese language sources to inform policy debate and advance public education. We specialize in open-source research using Chinese language sources to inform policy debate and advance public education. Configure NFSv3 Ports in RedHat. Configure NFSv3 Ports in RedHat. Configure NFSv3 Ports in RedHat.
The main reason is to support the developer for there hard work also for new stuff. The main reason is to support the developer for there hard work also for new stuff. The main reason is to support the developer for there hard work also for new stuff. If available please supply below. If available please supply below. If available please supply below. Nfsd is of course on port 2049 and the portmapper is on port 111. Nfsd is of course on port 2049 and the portmapper is on port 111. Nfsd is of course on port 2049 and the portmapper is on port 111.
Our core mission is to create and disseminate knowledge that makes the region more peaceful and prosperous. Our core mission is to create and disseminate knowledge that makes the region more peaceful and prosperous. Our core mission is to create and disseminate knowledge that makes the region more peaceful and prosperous. TCP is a connection-oriented protocol it requires handshaking to set up end-to-end communications. TCP is a connection-oriented protocol it requires handshaking to set up end-to-end communications. TCP is a connection-oriented protocol it requires handshaking to set up end-to-end communications. This is becus roblox updated every week and all the codes in the exploit are getting patched thats why the injection is broke at that moment thats why you need to check the website again to see if the exploit is updated this will also be told in the card of the exploit. This is becus roblox updated every week and all the codes in the exploit are getting patched thats why the injection is broke at that moment thats why you need to check the website again to see if the exploit is updated this will also be told in the card of the exploit. This is becus roblox updated every week and all the codes in the exploit are getting patched thats why the injection is broke at that moment thats why you need to check the website again to see if the exploit is updated this will also be told in the card of the exploit.
TCP port 2049 uses the Transmission Control Protocol. TCP port 2049 uses the Transmission Control Protocol. TCP port 2049 uses the Transmission Control Protocol.
If you re searching for 2049 Port Exploit you've reached the right place. We have 20 images about 2049 port exploit including images, photos, pictures, backgrounds, and more. In these page, we additionally have number of graphics out there. Such as png, jpg, animated gifs, pic art, logo, black and white, transparent, etc.

Source Image @ chowdera.com

Htb Blunder Htb Writeups
Source Image @ zweilosec.gitbook.io

Hackthebox Remote Writeup Jackhack
Source Image @ jackhack.se

Vulnhub Vulnix Ivan S It Learning Blog
Source Image @ ivanitlearning.wordpress.com